Safeguarding Your Digital World: 6 Key Cyber-Threat Areas for 2023 and Beyond
In today’s ever-evolving digital landscape, the task of ensuring protection is becoming increasingly complex. In this digital era, every organization, regardless of its size, is a potential target, facing the risk of breaches that could compromise its operations, brand reputation, and revenue streams.
As we navigate the challenges of the modern digital environment, the imperative to safeguard our systems and data grows stronger. With the digital realm expanding rapidly, organizations must recognize and address the evolving cyber threats that can undermine their security and resilience. In this article, we will delve into six critical areas of concern for companies and organizations, shedding light on the steps they should take to prioritize cybersecurity and ensure a robust defense against these threats.
Machine Learning and Artificial Intelligence: Driving a Digital Revolution
The current phase, known as the Fourth Industrial Era, is marked by unprecedented technological advancements, characterized by the fusion of the physical, digital, and biological worlds. This convergence encompasses cutting-edge technologies such as artificial intelligence (AI) and machine learning (ML), quantum computing, blockchain, and biotechnology. AI and ML, in particular, are revolutionizing various sectors, including cybersecurity.
Automation driven by AI and ML is redefining cybersecurity practices, enabling computers to perform tasks like speech recognition, learning, planning, and problem-solving. Predictive analytics powered by these technologies allow for data-driven risk reduction, optimizing resource consumption while enhancing security.
The Challenge of Polymorphic Malware
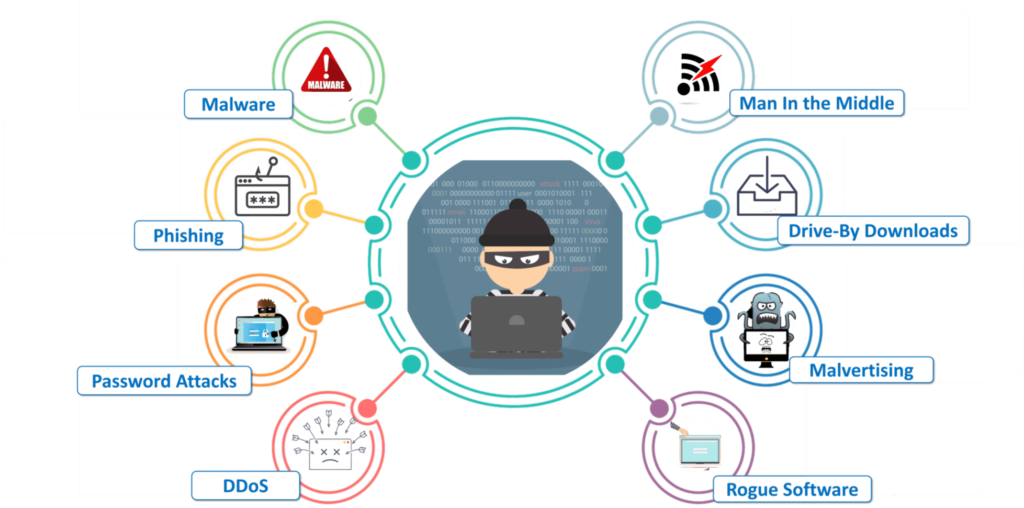
The emergence of polymorphic malware presents a significant challenge in the cybersecurity landscape. This type of malware is designed to continuously evolve, making detection and mitigation increasingly difficult. Leveraging machine learning algorithms and artificial intelligence, polymorphic malware adapts its form to evade traditional security measures.
Rather than aiming for efficiency, polymorphic malware focuses on avoiding detection. By making subtle modifications, it can elude recognition based on known characteristics, enabling numerous instances of the same malware to appear distinct. This form of malware can encompass ransomware, keyloggers, rootkits, and more, posing a serious threat to organizations.
Advanced Intelligent Botnets: A Growing Menace
Botnets, networks of compromised computers and devices controlled by hackers, pose a significant threat in the digital realm. These malicious entities can disseminate malware and ransomware, perpetuating self-replicating attacks. Hackers employ various methods to compromise devices, often targeting unprotected systems via Wi-Fi routers, web servers, and network bridges.
Advancements in AI and ML have enabled botnets to scale their attacks rapidly. Cybercriminals now utilize Bot-as-a-Service to outsource attacks, with Distributed Denial of Service (DDoS) attacks being a prevalent danger. These botnets not only imitate real users but also engage in activities like IP scraping, data theft, and overwhelming platforms.
Ransomware’s Persistent Grip
Ransomware continues to cast a long shadow over the cybersecurity landscape. This type of malware encrypts crucial files, rendering them inaccessible to victims, who are then extorted for payment in exchange for decryption. Ransomware attacks exploit vulnerabilities in digital commerce and the expanding attack surfaces, making it a preferred tool for cybercriminals.
The rise of ransomware has been propelled by evolving malware delivery methods and the adoption of cryptocurrencies for anonymous payments. Recovery times, ransom demands, and breach-related lawsuits are all on the rise, posing significant challenges for affected organizations. The Colonial Pipeline and SolarWinds breaches serve as poignant reminders of the devastation ransomware can wreak.
Securing Supply Chains
Supply chain vulnerabilities have long been exploited by cyber attackers. Weak links in the supply chain can be targeted by nation-state adversaries, criminals, or hacktivists. These attacks often leverage poor security practices, compromised hardware or software, and insider threats to infiltrate systems.
Recent incidents like the Colonial Pipeline and SolarWinds breaches underscore the need for robust supply chain cybersecurity. The interdependence of organizations within the supply chain makes addressing cyber threats a complex endeavor. A majority of IT professionals have identified substantial risks within their software supply chains, highlighting the need for comprehensive security measures.

Quantum Computing: Unleashing New Possibilities and Risks
The advent of quantum computing brings forth both transformative possibilities and significant risks. Quantum computers have the potential to decipher private information encrypted with traditional methods. Current cybersecurity protocols rely on pseudo-random number generation, a vulnerability that quantum computers can exploit.
As quantum computing develops, public key algorithms could become obsolete, a phenomenon known as QDay. Quantum computers could potentially disrupt cybersecurity by cracking conventional random number generation methods. This development poses geo-military threats and underscores the urgency for robust security measures.
Conclusion
In the digital age, cybersecurity remains an ongoing challenge, shaped by the relentless evolution of threats. Machine learning and artificial intelligence, polymorphic malware, advanced botnets, ransomware, supply chains, and quantum computing are focal points in this dynamic landscape. It is essential for organizations to be vigilant, informed, and proactive in their efforts to protect their digital assets. By prioritizing these six critical areas, businesses can fortify their cybersecurity defenses and navigate the complex digital terrain with greater resilience.